Distributed Intrusion Detection Using Windows Registry
Git RepoMay 2011 - April 2012
Reading time ~ 2 minutes
Developed client and server applications to detect any intrusion attempts in hosts connected in a LAN
About the project
A Host-based intrusion detection system monitors and analyzes the internals of a computing system as well as the network packets on its network interfaces.
Intruders often want to own the computer they have attacked, and will establish their “ownership” by installing software that will grant the intruders future access to carry out whatever activity (keystroke logging, identity theft etc.). We categorized all events as a) Normal, b) Monitor, c) Deny, and can be bought to the notice of an administrator by tapping this information in a log. We have done this using live windows registry monitoring, obtaining file system information, detecting the kind and type of hardware devices plugged into the system during runtime, scanning remote system ports etc.
We started with a basic file transfer program which helps in tamper-proof file transmission between any two computers in a local network, using an Access Control List.
Eventually, we used windows registry for following operations:
- Get the host side information such as the applications installed on the remote host.
- Enable/Disable hardware and software resources
- Remote Process kill which can be used by the administrator for killing any potentially dangerous process on a server residing on the network
- Password management and to disable/enable registry editing
- Registry restore
Administrator
Empowered with a ‘Remote process kill’ functionality to address the issues with rogue processes Can disable/enable hardware on select hosts, for instance USB
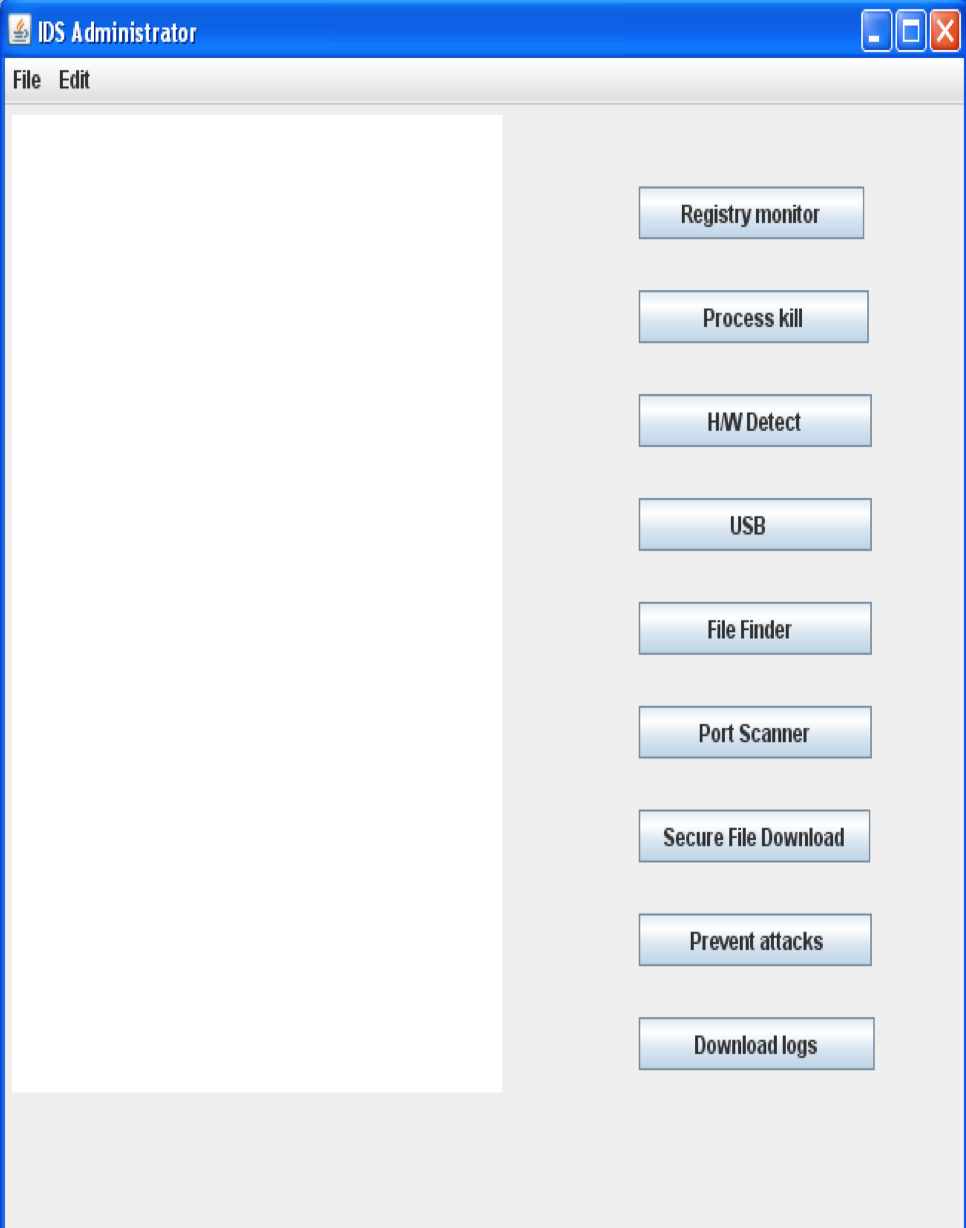
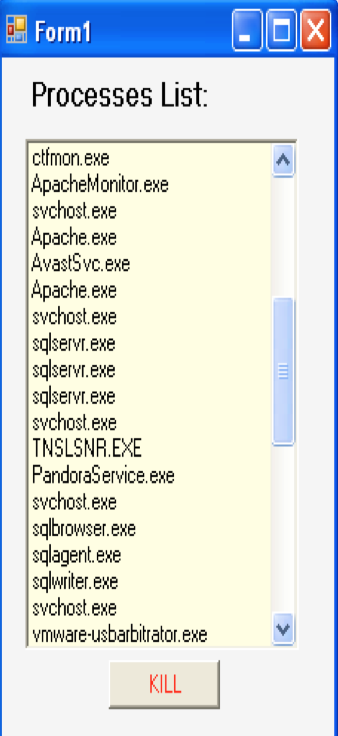
Hosts
We continuously scan the ports for malicious activity and also use a packet sniffer to dig out unexpected behavior.
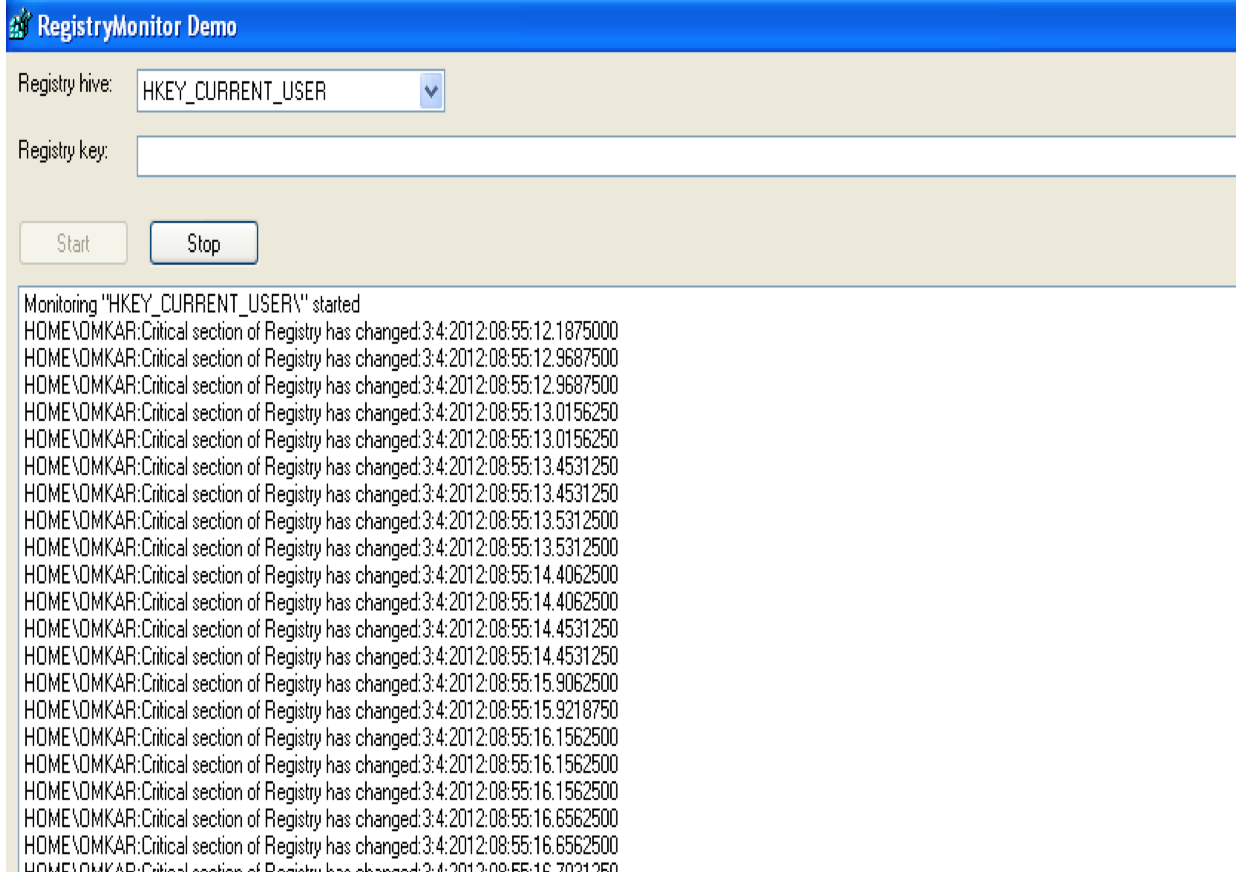
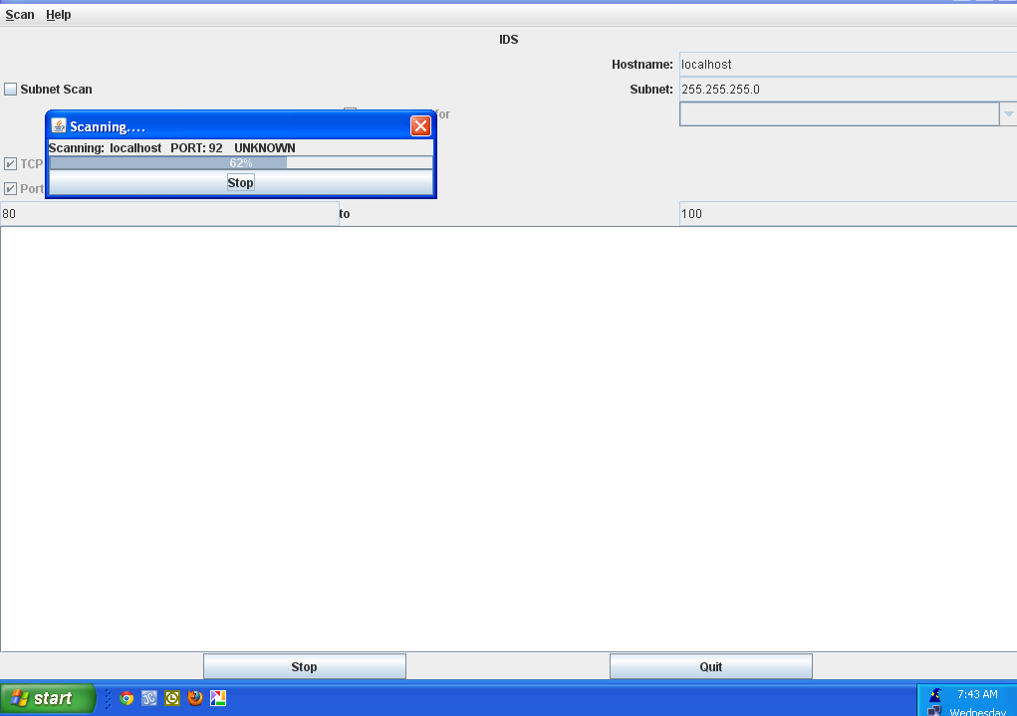
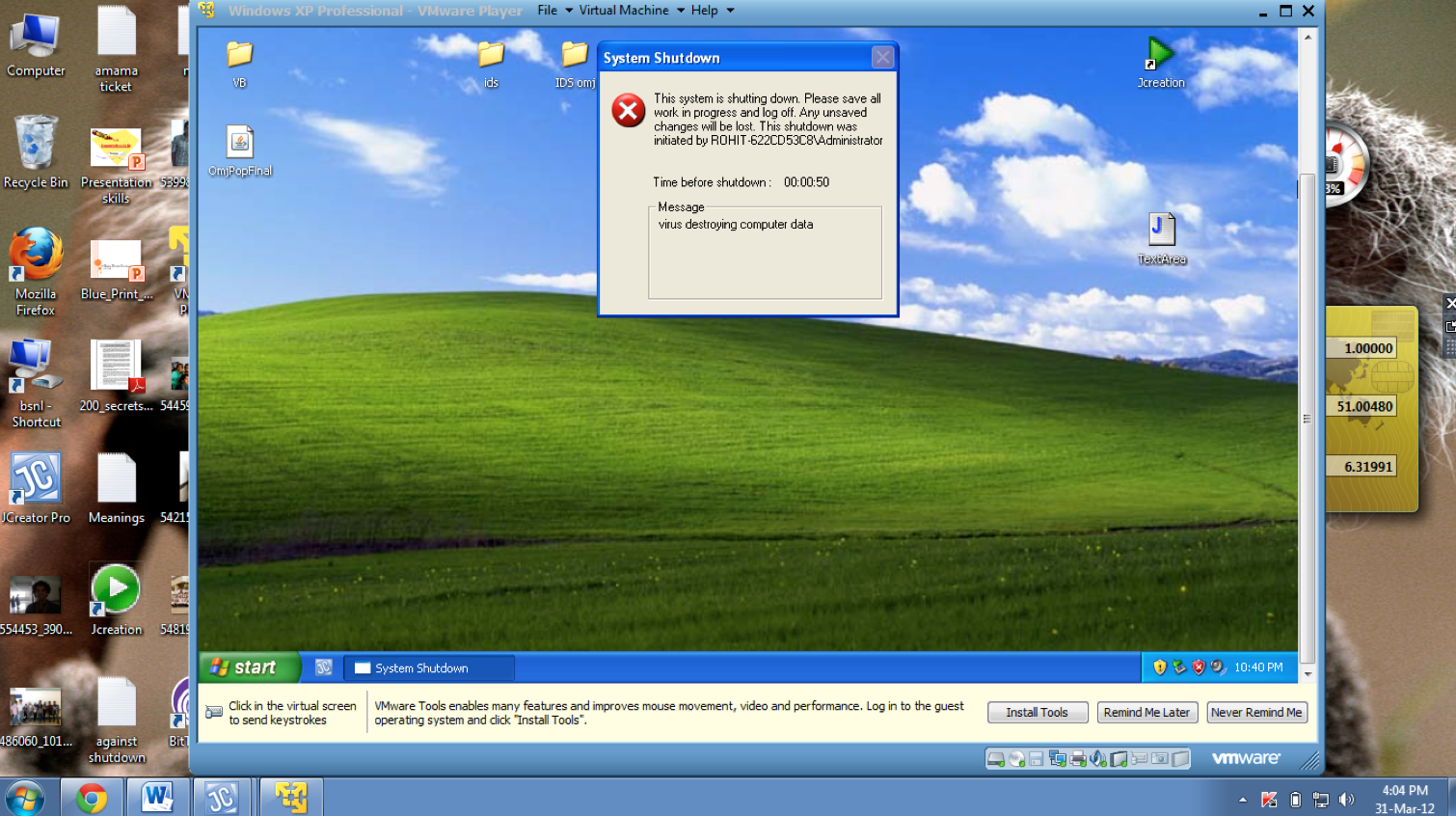
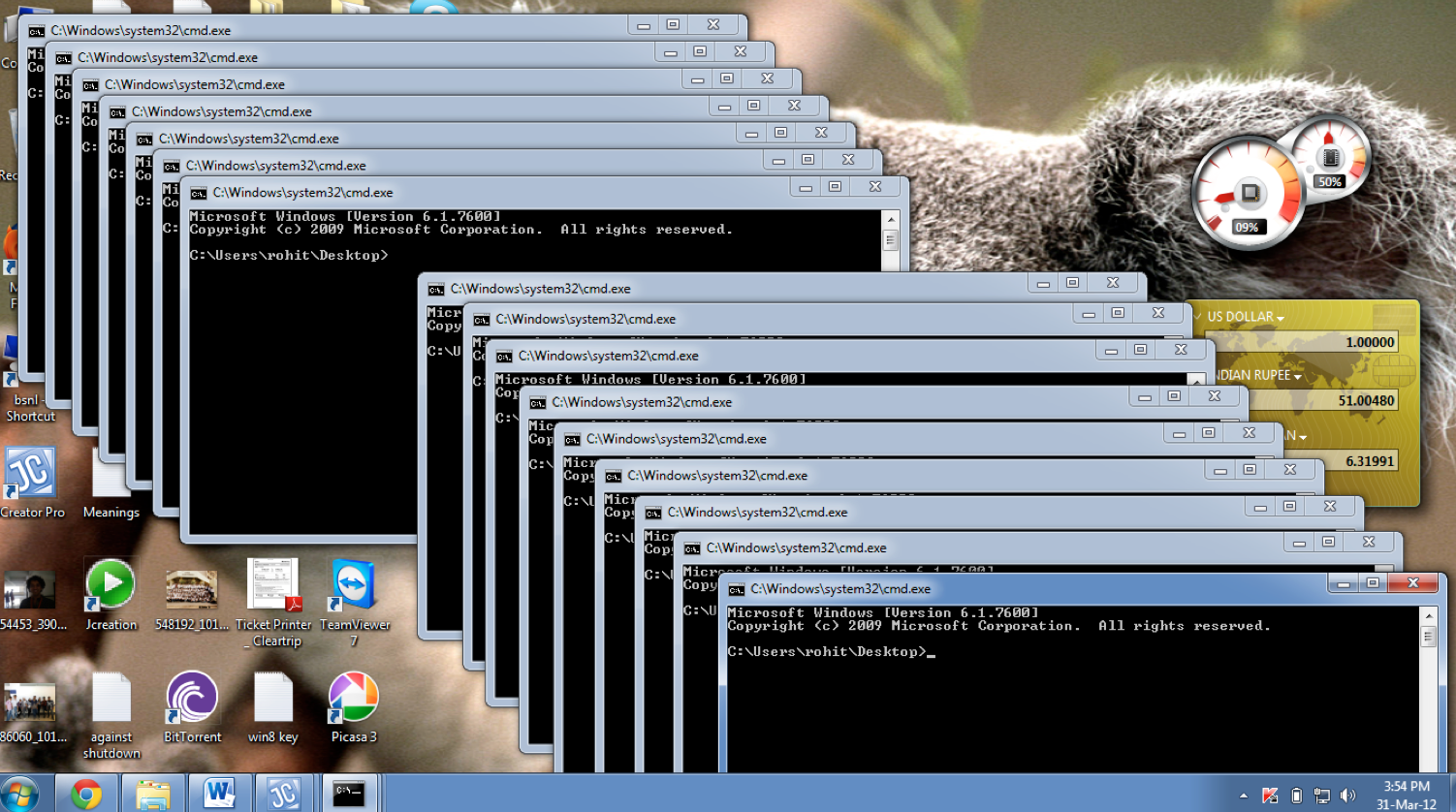
We handled many kinds of viruses such as auto-shutdown, infinite duplication of folders etc (pictures below), primarily using the virus signatures and monitoring windows registry
Team
- Rohit Nair
- Omkar Joshi